What Makes VeilAI Different
Current AI System
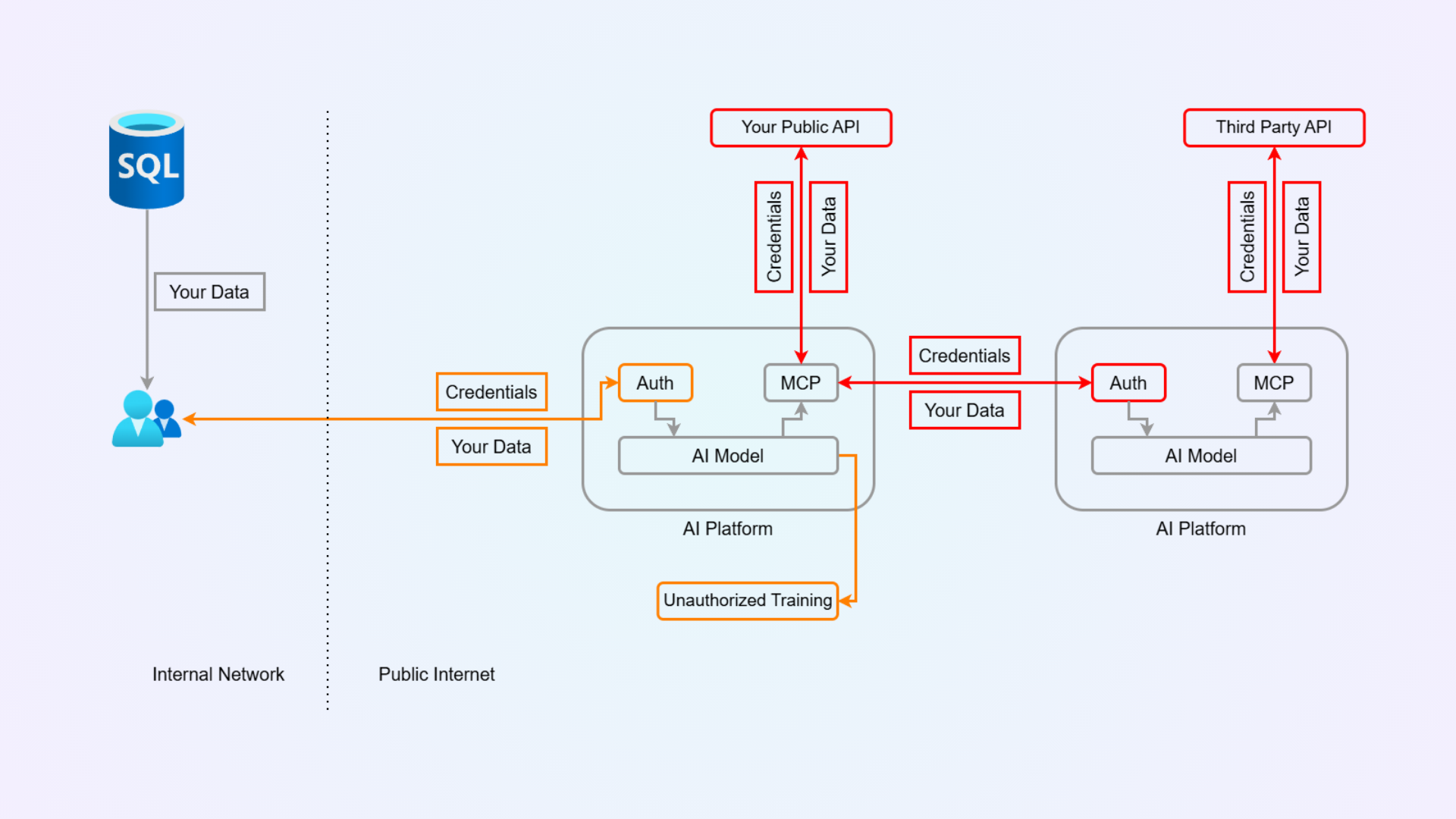
The Fundamental Security Flaw
Current AI systems suffer from an architectural security problem that no amount of authentication can solve: your data must leave your secure network to be processed by AI servers.
As illustrated in the diagram above, when you use a current AI platform, your sensitive data and credentials flow from your internal network across the public internet to the AI platform's servers. This happens regardless of how robust your authentication system is—whether you use OAuth, API keys, multi-factor authentication, or any other authentication mechanism.
Why Authentication Can't Fix This
Authentication systems are designed to answer one question: "Who is allowed to access this resource?" They cannot answer the more fundamental question: "Where is my data being processed and stored?"
This architectural flaw enables concrete exploits and attacks that authentication cannot prevent. Once your data leaves your secure network, it becomes vulnerable to multiple attack vectors:
Unauthorized Training Attack: As shown by the orange arrow from the AI Model to "Unauthorized Training," your proprietary data can be used to train models without your consent. This server-side operation occurs after authentication, making it invisible to traditional security controls. Your business data could be used to improve models that benefit your competitors—a critical competitive intelligence risk.
Server-Side Data Exposure: Even with perfect authentication, your data must be transmitted to and processed on the AI platform's servers. Once it reaches their infrastructure, it's out of your control. This creates opportunities for credential harvesting via man-in-the-middle attacks—the multiple credential flows (orange and red arrows) can be intercepted by attackers positioned between your network and the AI platform, or between your platform and third-party services. Even encrypted credentials must be decrypted at destination servers, creating attack surfaces.
Supply Chain Vulnerabilities: The red arrows showing data flow to third-party AI platforms represent a transitive trust problem. When your AI platform leverages third-party services, your credentials and data cascade through multiple systems. If any third-party platform is compromised, your data is exposed regardless of your primary platform's security posture. Each additional hop increases your attack surface exponentially.
Data Persistence and Exfiltration: Your data may be logged, cached, or stored on servers in jurisdictions you don't control. This enables log injection and data persistence attacks—attackers who compromise logging systems or gain access to log storage can extract sensitive information that was transmitted, even if the original request was properly authenticated. Additionally, data exfiltration via API abuse allows attackers with stolen credentials (through credential stuffing, token theft, or insider threats) to access previously stored or cached data server-side.
Multi-Tenant Isolation Failures: In multi-tenant AI platforms, your data is processed on shared infrastructure. Cross-tenant data leakage can occur through side-channel attacks, container escape vulnerabilities, or misconfigurations, allowing other tenants to access your data regardless of authentication boundaries.
These attacks are possible because the architecture fundamentally requires your data to exist on servers you don't control, creating persistent attack surfaces that authentication cannot eliminate.
The Root Cause
The problem isn't with authentication—it's with the centralized architecture itself. In a current AI system, intelligence is centralized in cloud servers, which means your data must travel to the intelligence. This creates an inherent security vulnerability that cannot be patched with better authentication, encryption in transit, or access controls.
The only way to truly solve this problem is to change the architecture: move the intelligence to your data, not your data to the intelligence.
VeilAI System - The Only Solution
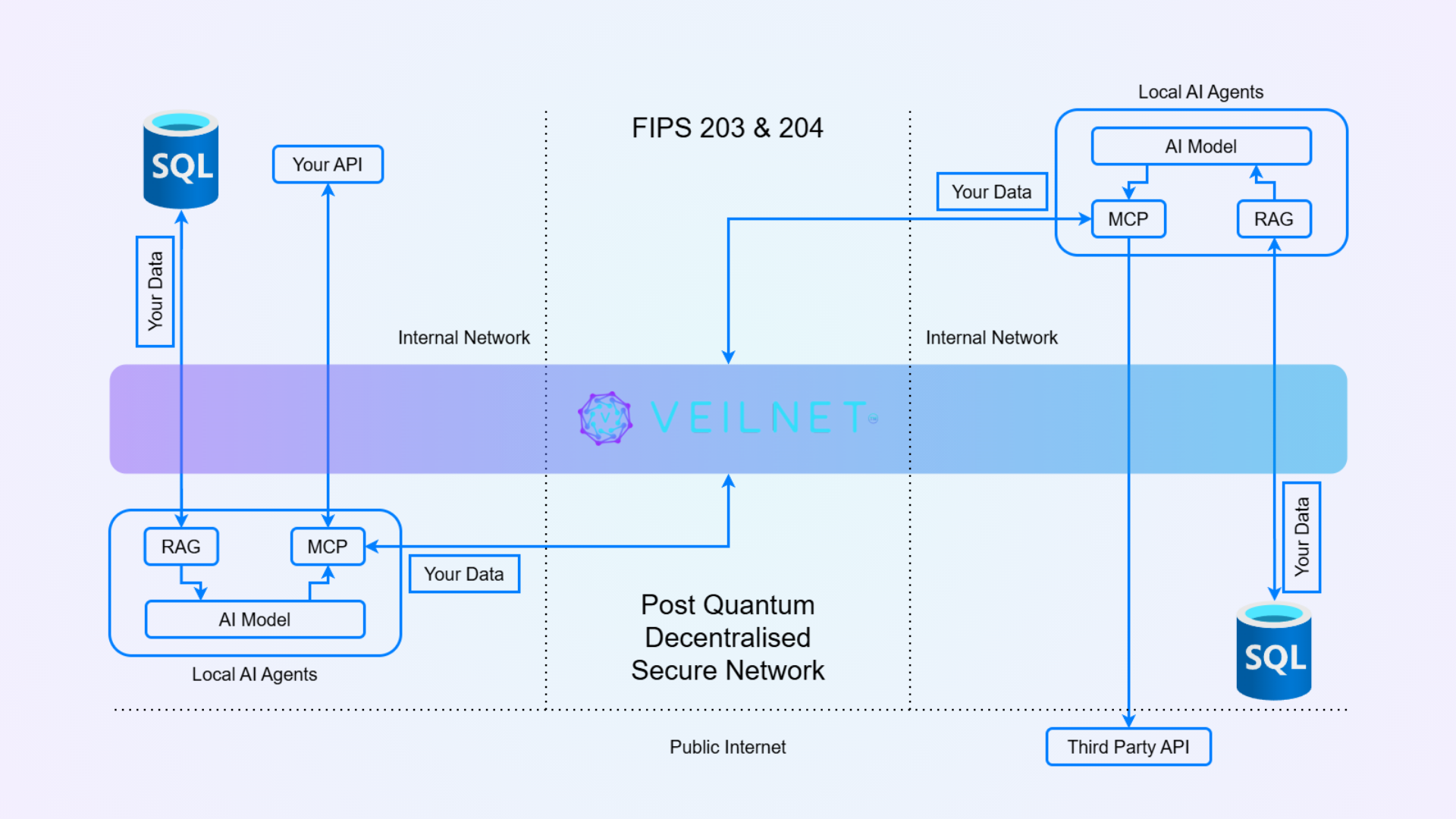
VeilAI fundamentally eliminates these security vulnerabilities by inverting the architecture: intelligence moves to your data, not your data to the intelligence. This architectural shift eliminates the attack surfaces that plague current AI systems.
How VeilAI Eliminates Each Threat
Unauthorized Training Attack - Eliminated: In VeilAI's architecture, your data never leaves your internal network. Local AI Agents process your data within your controlled environment, using RAG (Retrieval Augmented Generation) to access your SQL database directly. Since your proprietary data never reaches external servers, it cannot be used for unauthorized training. The AI models run locally, ensuring your competitive intelligence remains yours alone.
Server-Side Data Exposure - Eliminated: VeilAI's Local AI Agents process all sensitive data within your Internal Network boundary. As shown in the diagram, your data flows from your SQL database to your Local AI Agents (RAG, MCP, and AI Model components), all operating within your secure perimeter. Data never crosses into untrusted server infrastructure, eliminating the risk of server-side exposure entirely.
VeilNet adds an additional layer of protection by creating a local air-gap through its virtual network. Even if your internal network is compromised, your data and AI system remain secure. This is achieved through packet-level authentication (PLA) with Dilithium digital signatures (FIPS 204).
In VeilNet, every AI agent, API endpoint, and component creates its own unique post-quantum cryptographic identity. This cryptographic identity is embedded in every network packet, eliminating the need for traditional authentication systems, credentials, API keys, or tokens. Unlike traditional authentication that protects at the application layer and requires credentials to be transmitted and validated, VeilNet's packet-level authentication determines whether an IP packet should exist at all before it has a chance to reach application layer logic. Only packets with valid cryptographic signatures are accepted at the network layer. This means packets from unktrusted sources will not reach the application layer, providing defense-in-depth that protects your AI infrastructure even in compromised network environments—all without the attack surface created by credential management systems.
Supply Chain Vulnerabilities - Eliminated: VeilAI still utilizes third-party APIs when needed, but with a critical architectural difference: VeilAI only acts as a client. Your Local AI Agents initiate outbound connections to third-party services when you need them, but third parties have no way to establish connections back into your system when you don't need them. This unidirectional, client-initiated architecture eliminates the transitive trust problem. Unlike current AI systems where third-party platforms can receive your data through cascading service dependencies, VeilAI maintains complete control over when and how third-party services are accessed. When collaboration between AI agents is needed, it occurs through the secure VEILNET infrastructure with FIPS 203 & 204 compliance. Each component's post-quantum cryptographic identity ensures that only authorized agents can participate in the network, eliminating the need for credential exchange and ensuring no unauthorized inbound access to your infrastructure.
Data Persistence and Exfiltration - Eliminated: Your data is processed in-memory by Local AI Agents and never persists on external servers. There are no external logs, caches, or storage systems that could be compromised. Even when data flows through VEILNET for distributed processing, it's handled through post-quantum secure channels without persistent storage. When third-party APIs are accessed, your Local AI Agents make client-initiated outbound requests only—there are no persistent inbound connections or endpoints that could be exploited for data exfiltration. This eliminates the risk of credential theft or unauthorized data access from external API endpoints.
Multi-Tenant Isolation Failures - Eliminated: VeilAI's architecture eliminates multi-tenant risks entirely. Each organization runs their own Local AI Agents within their own Internal Network. There is no shared infrastructure, no container escape vulnerabilities, and no side-channel attacks possible because your data never coexists with other tenants' data. You maintain complete isolation and control.
The Architectural Foundation
VeilAI's security is built on three foundational principles:
- Local Processing: AI models, RAG systems, and MCP components run as Local AI Agents within your Internal Network, ensuring data never leaves your control.
- Post-Quantum Secure Network with Packet-Level Authentication: VeilNet provides a decentralized, post-quantum secure network (FIPS 203 & 204 compliant) that creates a virtual air-gap through packet-level authentication using Dilithium digital signatures. Every AI agent, API endpoint, and component connected through VeilNet possesses a unique post-quantum cryptographic identity. This identity-based architecture eliminates the need for traditional authentication systems, credentials, or API keys—each packet is cryptographically signed by the sender's post-quantum identity, and network-layer validation ensures only authorized identities can communicate. This network-layer protection ensures that even if the internal network is compromised, unauthorized packets are rejected before reaching application logic, providing defense-in-depth for distributed AI operations without the vulnerabilities inherent in credential-based authentication systems.
- Data Sovereignty: Your data remains in your SQL databases, accessed only by your Local AI Agents. Intelligence comes to your data, not the other way around.
This architecture doesn't just mitigate risks—it architecturally eliminates them. By ensuring your data never leaves your secure network, VeilAI removes the fundamental attack surfaces that authentication-based security cannot address. The threats simply cannot occur because the vulnerable architecture doesn't exist.
